|
|
|
|
|

Feasibility Study Site for JVNRSS and RSS Extension
|
|
|
|
| Table of Contents |
|
|---|
|
|
|
| TRnotes update | [top] |
|---|
|
|
|
| Topics | [top] |
|---|
| March 28, 2006 | : | Registration of site name (jvnrss.ise.chuo-u.ac.jp) |
| March 30, 2006 | : | Start of site construction |
| June 30, 2006 | : | Launch of JVNRSS feasibility study site |
| August 02, 2006 | : | Directory of FIRST Teams' RSS [ FirstRSS ] published. |
| August 13, 2006 | : | TRnotes update published. |
| September 17, 2006 | : | CVSS V1.0 Calculator for Server (Ver1.0) published. |
| September 22, 2006 | : | XML Verify Tool for SIG_rdf (Ver1.0) released. |
| September 23, 2006 | : | XML Sign Tool for SIG_rdf (Ver1.0) released. |
| November 13, 2006 | : | CVSS V1.0 Calculator for PC (Ver1.0) released. |
| January 1, 2007 | : | XML Sign Tool for SIG_rdf (Ver2.0) released. |
| January 5, 2007 | : | JVNRSS/RSS/Atom Flash Viewer released. |
| May 4, 2007 | : | "application/xml" is assigned as MIME Type of "extensions: xml xsl xsd rdf atom". |
| July 27, 2007 | : | CVSS V2.0 Calculator for Server published. |
| August 21, 2007 | : | CVSS V2.0 Calculator for PC released. |
| May 26, 2008 | : | MyJVN project started. |
|
|
|
| About JVNRSS activity | [top] |
|---|
This site is feasibility study site for JVNRSS (JP Vendor Status Notes RSS) activity. [5][6]
- CVE+: CVE+ is to make a relationship map between CVE and Japanese security information.
- CVSS: CVSS is study to collaboration possibilities between JVNRSS and CVSS.
- RSS_dir: RSS_dir is concept of RSS directory for RSS channel. RSS directory describes a RSS channel tree with RSS format.
- SIG_rdf: SIG_rdf is to provide JVNRSS with XML signature.
- TRnotes: TRnotes provides HTML based information, JVNRSS format and Visualized TRnotes.
- XSL_swf: XSL_swf is FLASH tool for visualized JVNRSS and uses a part of XSL as a mechanism to describe how the document should be displayed.
| |
RSS is an XML-based format that allows the consolidation of the lists of hyperlinks. The original RSS, version 0.90, was developed by Netscape as a format for building the portals of headlines for the major news sites. RSS 1.0 was based on RDF (Resource Description Framework) and designed by the original guiding principles of RSS 0.90.
| |
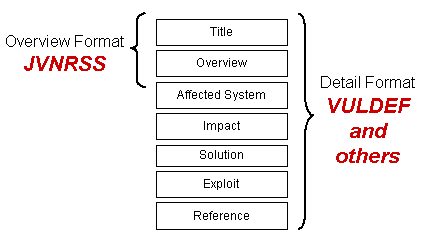
EISPP [1], CAIF [2] and VULDEF [3] are the XML formats to describe the details of security information and JVNRSS [4] is an XML format based on RSS to describe the overview of those formatted security information.
|
| |
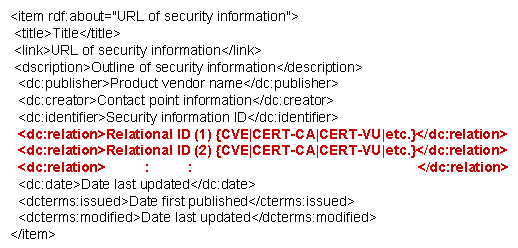
JVNRSS is based on RSS 1.0 and uses the field <dc:relation> of the Dublin Core as a primary key to group security information [1]. JVNRSS with the Relational ID in <dc:relation>. RSS contains a list of items, each of which is identified by a link. Each item can have any amount of metadata associated with it. The most basic metadata supported by RSS includes a title for the link and a description of it. Our proposed Relational ID allows the security information from the different websites to correlate with each other.
|
|
Making use of JVNRSS is an essential point in the security information exchange, for this handily resolves the following two basic issues:
Distribution designed to encourage reuse of information
Our primary objective is to aggregate security information from the product vendors and provide it through the JVN website. But in order to reuse published information, it must be offered in a machine-readable format. This is where RSS comes in. By using RSS, JVN data can be distributed in the same way just as the news feeds provided by the news websites. And because the content is described by RSS, it can be easily verified if information has been added to an item or an item has been updated.
More efficient aggregation of information from product vendors
JVN aggregates security information from the product vendors received via e-mail notifications. But in order to enlist the participation of as many product vendors as possible, an efficient means of collecting information other than e-mail must be also set up. Use of RSS will enable information to be collected from the product vendor's website and be automatically combined with other security information at the JVN website.
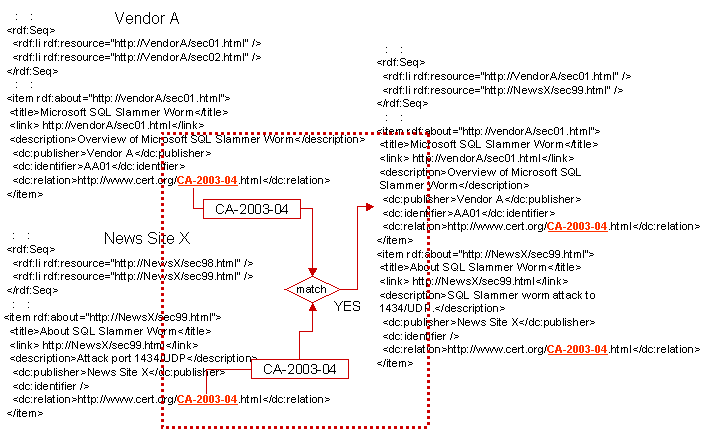
For example, when the grouping mechanism finds <item> with the same Relational ID, it makes these <items> into a group. When the grouping mechanism does not find any <items> with the same Relational ID, it will try to find a matching Relational ID using the Mapping DB (See CVE+).
|
|
[1] European Information Security Promotion Programme, http://www.eispp.org/
[2] Common Announcement Interchange Format, http://cert.uni-stuttgart.de/projects/caif/
[3] VULDEF: Security Advisory Publication Format, http://jvnrss.ise.chuo-u.ac.jp/jtg/vuldef/
[4] JVNRSS - JP Vendor Status Notes RDF Site Summary, http://jvnrss.ise.chuo-u.ac.jp/jtg/jvnrss/
[5] Proposal of the Security Information Sharing System with RDF Site Summary, The 8th World Multi-Conference on Systemics, Cybernetics and Informatics, Vol.X, pp.40-46 (Jul.18-21, 2004)
[6] Proposal of RSS Extension for Security Information Exchange, 18th Annual FIRST Conference (June 25-30, 2006), http://www.first.org/resources/papers/conf2006.html#p187
|
|
|
| About JVN | [top] |
|---|
|
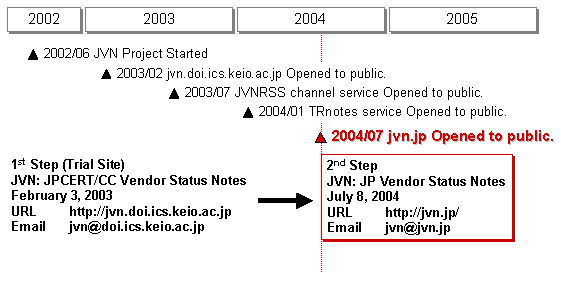
In Japan we hadn't had a function like the CERT/CC Vulnerability Notes Database that collected security information. To improve this situation, the JVN (at this point called JPCERT/CC Vender Status Notes Database) was created in February 2003 with the support of the JPCERT/CC. We designed the JVN as a portal site to provide information on vulnerabilities in software products used in Japan. The purpose of the database is to provide the latest information about the vulnerabilities in the domestic software products and help users deal with those vulnerabilities. Although information about vulnerabilities per se has been already disseminated in the form of the security hole reports put out by many organizations and vendors, the database greatly enhances the usefulness of the information by also including the updates and the status reports on the latest efforts by the product venders to deal with vulnerabilities. The primary purpose of the JVN Database is to collect and disseminate these information.
| |
In July 2004, the Ministry of Economy, Trade and Industry (METI) adopted the "Standard for Handling Software Vulnerability Information" as an official rule, and began promoting the "Information Security Early Warning Partnership" as an implementation framework [1]. The JVN has become the portal site to provide the security information about the domestic computer software and hardware manufactured by the vendors registered in the framework [2]. Launched with the support of the JPCERT/CC on the basis of its successful feasibility study, the JVN has become a joint venture by IPA and JPCERT/CC within the official framework. Subsequently, the name of the organization was changed to "JP Vendor Status Notes," but the original acronym JVN was retained, and the portal site for publishing the status of the vendor's effort dealing with the domestic software vulnerabilities has also been kept as it was.
|
| |
JVN provides the "Vendor Status Notes (VN)" and the "Status Tracking Notes (TRnotes)". VN is a service providing information on how to fix vulnerabilities. It is similar to the "CERT Vulnerability Notes" and follows up the IPA/JPCERT Vulnerability reports, US-CERT Alerts, US-CERT Vulnerability Notes and NISCC Advisories. TRnotes is a service providing information on the incidents, specifically what worms do, when the exploit codes were released and what the countermeasures are.
|
[1] Information Security Early Warning Partnership, http://www.ipa.go.jp/english/security/third.html
[2] JP Vendor Status Notes, http://jvn.jp/ (in Japanese)
[3] Deploying JP Vendor Status Notes (JVN) for Dissemination of Security Information Throughout Japan, http://www.sdl.hitachi.co.jp/english/people/jvn/
|
|
|
| Acknowledgements | [top] |
|---|
|
|
|
| JVNRSS Feasibility Study Team | [top] |
|---|
The members of JVNRSS Feasibility Study Team:
Masato Terada, Hitoshi Takasaki, Chika Nukui and JVN Working Group (JPCERT/CC, IPA).
|
|
|
|
|