| Table of Contents | [top] |
|---|
|
|
|
| Overview | [top] |
|---|
CVE+
CVE is a list of standardized names for vulnerabilities and other information security exposures.
Currently CVE mostly doesn't include security information published by Japanese vendors, because Japanese vendors don't post security information in a CVE-compatible format.
CVE+ is to make a relationship map between CVE and Japanese security information.
The grouping module extracts the Relational ID of JVNRSS feed <item> and finds the CVE entry with the same Relational ID.
Some modules in Figure have been implemented as a Proof of Concept prototype.
Also the convert module produces a TouchGraph XML format and RSS Extension (mod_sec) format to describe the relationship map.
| |
|
Our gathering and grouping approach using the JVNRSS format has three steps.
Gathering of the security information
The gathering module periodically checks changes in JVNRSS feeds on other Web sites and extracts the JVNRSS items upon change.
Grouping of the security information
The grouping module extracts the Relational ID from the JVNRSS feed <item>. This module checks other JVNRSS feed items using Relational ID as the search key.
When the module finds <item> with the same Relational ID, it makes these <item> into a group.
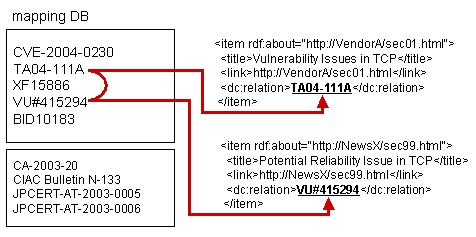
When this module does not find any item with the same Relational ID, it will try to find a matching Relational ID using the Mapping DB.
The upper group in the mapping DB shows the vulnerability information related to the TCP stack and the lower group shows the incident information about the MS-Blaster worm. The items on the right, which refer to the same vulnerability or incident, belong to the same group. In case the feed <item> have a different Relational ID yet refer to the same vulnerability, the mapping DB traces the relationship between those Relational IDs.
Convert XML to HTML
The Convert module transforms XML documents into a HTML form to present security information.
|
|
|
|
| Data format | [top] |
|---|
|
|
|
| Viewer | [top] |
|---|
|
|
|
| Mapping DB data source | [top] |
|---|
|
|
|
| Archives DB data source | [top] |
|---|
|
in Japanese (lang=ja)
in English (lang=en)
|
|
|
| Revisions | [top] |
|---|
- Published.: 2006-04-23T02:50:00-00:00
|
|
|
|